Forums
Home › Forums › Feature Suggestions › AdBlock/Blacklist Granularity
AdBlock/Blacklist Granularity
- This topic has 4 replies, 2 voices, and was last updated 4 years, 12 months ago by
support.
-
AuthorPosts
-
July 4, 2020 at 10:56 pm #3970
Jake
ParticipantThe current blacklist needs some feedback and better details. Firstly, is it blocking incoming or outgoing packets, from a source or a destination, tcp and/or udp, does it drop or deny? Are there any predefined “allow” filters that that will override a blacklisted address? What is the required syntax (new line, address, comma/colon separated, etc.)? Can it filter Ports, or IP addresses? Can it filter Blocks of IP addresses?
I have tried and failed to block large ranges of addresses. For instance, I tried to block 23.192.0.0/11 using the blacklist and it has no effect. I’m constantly getting scanned by something on one of 4 servers including one in this CIDR range. I still need to setup a computer firewall to drop them. My efforts in the router failed.
I would rather see a menu layout for the adblocker feature. Something like an ‘advanced setup’ feature. I would like to be able to up/download a text file, or even link a github repository that contains a block list. As far as feedback for the blacklist, perhaps you could add a way to enter a single specific entry with a simple test. If the entry is a range, return the number of addresses in that range as a type of confirmation that the block of addresses is correct. It would be nice to know if all entries block tcp/udp/incoming/outgoing by confirmation even if it’s printing a string for blocks of addresses. If the user enters a single address, it would be nice if you setup a simple ping request or other verification to confirm a valid entry.I also wish the mac address filters included the entire network stack. Anything wired on the Ethernet setup is not filtered by the mac address. I would prefer to setup an SSH filter based on both static IP and mac address.
Next, try downloading icecat and if you really want to be a rockstar, elinks. Both of these can not login to the router, I think due to JavaScript. I like elinks because there’s no ambiguity, just text.
The last idea I’ll mention is a more detailed but user friendly way to modify the blocked list and log history. The easiest change needed is a page where both are visible at the same time. It would also help to see which addresses were served to which device and when. Any possible passive feedback available to the user would also be welcome. I don’t want any kind of external or online interface for the router, but it would be really great if there were a better way to figure out when an ad is being served with a mechanism that makes it easy to blacklist. Such an interactive mechanism might make it possible to make a practical whitelisted firewall system implementation.
Thanks in advance for taking the time to reply.
-JakePS, if I want to try openwrt on the router, is the software available to reload pcwrt?
July 7, 2020 at 4:35 pm #3971support
Keymaster@jake Blocking is mostly outbound. Inbound connections are automatically blocked by the firewall, unless the port is specifically opened with port forwarding. Inbound packets are DROPped unless the port is open.
Are you saying that you have open ports on your network and those open ports are constantly scanned by hosts from 23.192.0.0/11?
July 7, 2020 at 7:20 pm #3978Jake
ParticipantDo I have open ports being scanned? -No
Once a browser is opened, regardless of the activity/inactivity/website visited I noticed there was a large volume of data transferred constantly to one of 4 CIDR servers. Upon searching these, they show up in some known ads block lists. They primarily pull encrypted packets across HTTP. Even with HTTP disabled in UFW, it was still transfering hundreds of megabytes every few seconds. I finally blocked all of the TCP connections with an IPTable filter that blocks all the ranges, including incoming, outgoing, forwarding, and established. I can still see the dropped UDP packets in my log. They have random IP addresses in the CIDR range and they do odd things like lots of invalid addresses. At least as it is logged the IPV4 address is transposed into a IPV6 in random ways, and otherwise incomplete addresses are used. I thought perhaps the entire issue was some addon, but it happens even when these are removed. Blocking all of these addresses has no effect on the websites I visit. Using Whois on the IP ranges shows nothing about my ISP. I know their IP and servers from browsing shodan. The servers in question are all in the US but none are even in my region. The most common block of addresses sometimes resolves as Amazon aws in logs and the server is registered at MIT. The logs show a udp packet dropped around every 3 seconds. I had rather block this traffic from the network completely if possible. I have Firefox containerized, so the traffic is killed as soon as I close the browser. I just made the switch to Fedora Silverblue as well, so I KNOW I’m in control.
This is all a curiosity more than anything. I’m interested in a career in hardware development and looking at how to lock down a system as much as possible. My interests have been in embedded hardware/firmware/RTOS systems, not networking or security. This subject is a tangential distraction, turned curiosity. It’s possible I misunderstand some aspect of this and am chasing a non issue. It is odd that blocking this information causes no issues with the sites requested, and just the act of opening a browser to any web page results in the near constant flow of hundreds of megabytes of data. I’ve done the TCPdumps and checked them with Wireshark. It’s all just a garbled encrypted mess.
So no, I don’t have open ports,.. until I open a browser.July 8, 2020 at 4:40 am #4008support
Keymaster@jake This does not sound like normal browser behavior. Does this happen to all your browsers across all platforms?
On the router you can enter the CIDR IP address range as
23.192.0.0/11!in the black list. This is the “force block” syntax. I.e., both direct IP address requests as well as domains resolving to these IP addresses are blocked. More info on the black/white list syntax is available here: https://www.pcwrt.com/2020/01/how-to-allow-or-block-web-sites-on-the-router/.July 10, 2020 at 10:13 pm #4010support
KeymasterJust FYI. Some of the IP addresses in the IP address range
23.192.0.0/11are those of CDNs. Blocking this range will break some websites. For example, msn.com.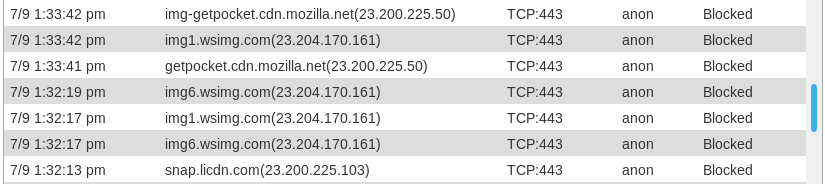
-
AuthorPosts
You must be logged in to reply to this topic.