-
How to create your SSH key and use it on the router
- Generate your key pair
Open a command line window and enter:
ssh-keygen -b 4096 -t rsaA pair of private/public keys will be generated under the .ssh folder. By default the file names are
id_rsaandid_rsa.pub. You can optionally enter a passphrase for your private key. - View your public key
On Linux or MacOS:
cat .ssh/id_rsa.pubOn Windows:
type .ssh\id_rsa.pub - Copy the public key to the router admin page
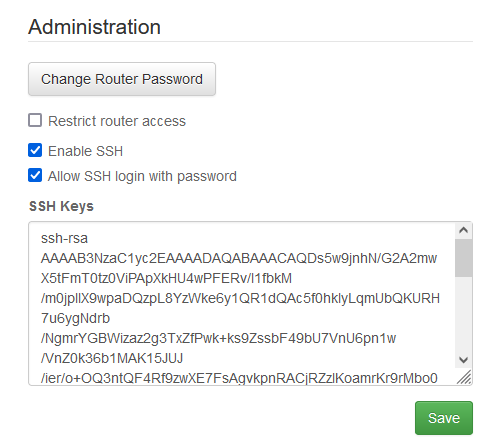
- (Optional) Start the ssh-agent and add your key to it.
If you’ve chosen to enter a passphrase for you private key but don’t want to enter the passphrase every time you use ssh, you may add your private key to the ssh-agent.
- Enter the command “
ssh-agent” to start the SSH Agent - Add your key to the SSH agent with
ssh-add ~/.ssh/id_rsa - To list the keys added to the SSH agent:
ssh-add -L
- Enter the command “
- Generate your key pair








After following these directions on macOS I am unable to login without using this terminal command
`ssh -oHostKeyAlgorithms=+ssh-rsa [email protected].1`
Thanks for sharing this.
After using that command I am still asked to verify the fingerprint.
16:52:47.272 iMac191
➜ ssh -oHostKeyAlgorithms=+ssh-rsa [email protected].1
The authenticity of host ‘192.168.10.1 (192.168.10.1)’ can’t be established.
RSA key fingerprint is SHA256:redacted.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])?
It seems that macOS needs to store these keys in the “known_hosts” file in .shh? Adding them to the SSH agent doesn’t seem to work.
The key generated here is used for authentication (i.e., in lieu of your ssh password). It’s not the ssh host key.
Your ssh client will ask you to confirm the host key only when you try to log in for the first time. It will not ask again once the host key is added to known_hosts.