-
Does your parental control pass the DOH test?

Why does DOH (DNS over HTTPS) interfere with parental control?
Unlike traditional DNS queries, which are sent to servers via a plain text connection, DNS-over-HTTPS (DoH) requests are sent over an encrypted HTTPS connection. It was introduced mainly because of the privacy benefits that come with the data encryption.
However, since many parental control systems depend on inspecting the unencrypted DNS requests, DOH brings real risk of breaking your parental controls. This is a big concern. In fact, Mozilla was once nominated for the Internet Villain Award for supporting DOH.
In an effort to keep existing parental controls functional in the brave new world of DOH, Mozilla implemented several opt-out mechanisms to bypass DOH for networks with DNS content filtering.
Is your parental control broken?
Is your parental control system still functional with DOH turned on? How effective are Mozilla’s mitigation techniques at keeping your parental control functional?
Nothing is better than trying it out for yourself.
The test steps
I’m using OpenDNS as an example. If you have a different setup, use the following steps as a starting point.
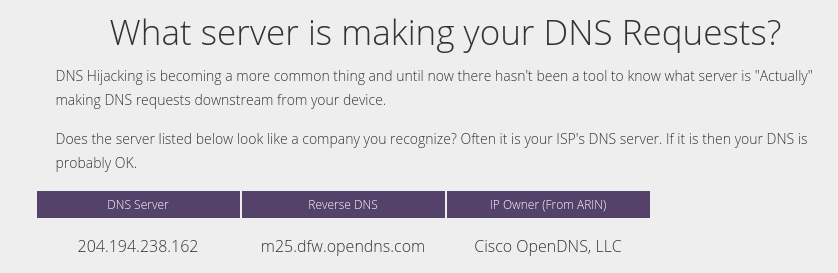
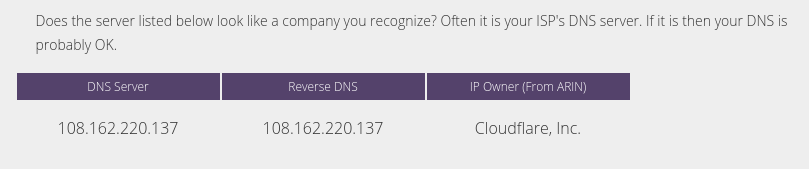
- What’s your DNS server? Open your browser and enter http://whoismydns.com/.
Since my network was configured to use OpenDNS, the page reported OpenDNS as expected.
- Turn on DOH in Firefox. In the Firefox browser:
- Open the Preferences page.
- Scroll down to the Network Settings section.
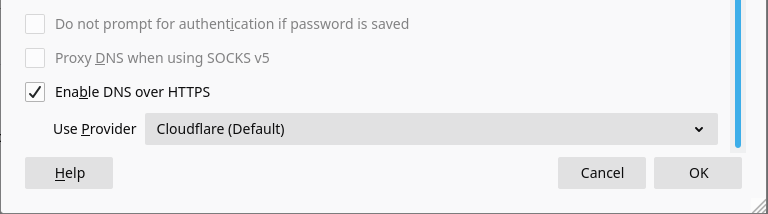
- Click on the Settings… button to bring up the Connection Settings dialog.
- Check Enable DNS over HTTPS, then select Cloudflare.
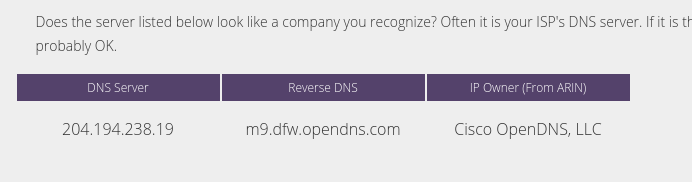
- Check the DNS server again. For my test, the page reported OpenDNS again. So OpenDNS filtering was still effective.
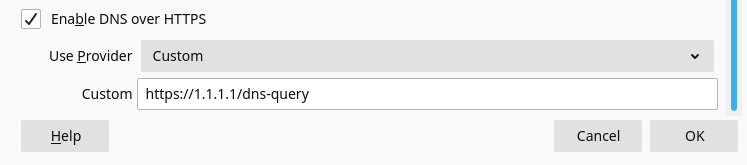
- Change the DOH server to Cloudflare IP address. Open the Firefox Connection Settings dialog again. Select Custom in Use Provider, then enter https://1.1.1.1/dns-query
- Check the DNS server again. This time my DNS server was changed to Cloudflare. OpenDNS filtering was no longer effective!
Other test scenarios
DNS over HTTPS (DOH) is supported by a growing number browsers and operating systems. For example, the Chrome browser also supports DOH. So does Android 9 and above, iOS 14 and macOS 11, etc. Windows 10 will have it soon if it’s not already there.
DOH’s sister protocol, DNS-over-TLS (DoT, which achieves the same effects as DOH), is also supported on these platforms.
The following picture shows how to turn on DoT on an Android phone.
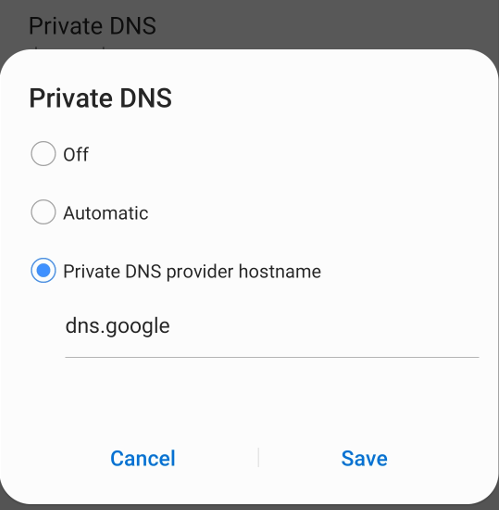
You may need to adjust the test steps above accordingly if you are not using Firefox and OpenDNS. The DNS server test may still be meaningful even if your parental control does not use a specific DNS service for content filtering.
There are other test scenarios you may want to consider:
- Try Google image search before and after turning on DOH/DoT.
- Try to visit a forbidden site before and after turning on DOH/DoT.
- Try a blocked app on a phone or a tablet before and after turning on DOH/DoT.
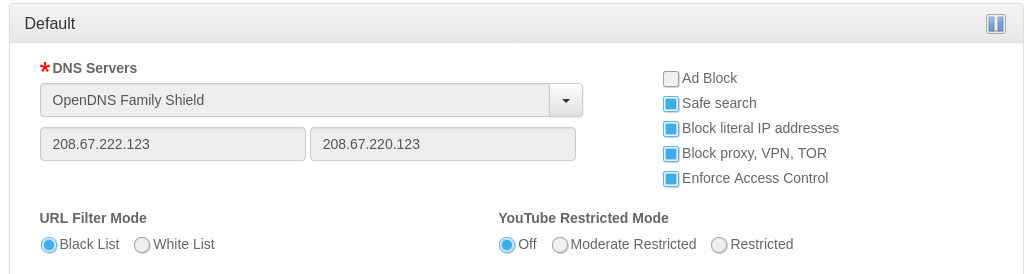
What can you do on the pcWRT router
On the pcWRT router, if you check the Enforce Access Control box on a profile, the router will force the devices to use the DNS service selected on the profile. Enabling (or hard coding) DoH/DoT on client devices will not bypass Access Control.
Summary
Parental controls may be broken when DOH or DoT is turned on. You may follow the steps above to test your system. OpenDNS has some builtin defense against DOH/DoT, but it’s easily defeated by entering an IP address for the DOH server instead of using the domain name.
- What’s your DNS server? Open your browser and enter http://whoismydns.com/.








I tried this test on my Gryphon parental control router. It failed miserably! As soon as I entered dns.google into my Android phone, the Internet was wide open. You can get to any porn site you want to, playboy, pornhub, you name it!
To make it worse, Gryphon reported the porn sites blocked even when they were wide open!