-
Five WiFi security settings and their effectiveness in securing your WiFi network
 Technologies change fast, what was once considered safe and secure may become vulnerable and obsolete by today’s standards. Here I’ll show five wireless security settings generally available on a WiFi router, and their effectiveness in securing your WiFi network.
Technologies change fast, what was once considered safe and secure may become vulnerable and obsolete by today’s standards. Here I’ll show five wireless security settings generally available on a WiFi router, and their effectiveness in securing your WiFi network.- Disable SSID broadcast.
It is often recommended that you should disable SSID broadcasting to make your WiFi network more “secure”. After all, when SSID broadcasting is disabled, hackers won’t be able to see your network and therefore, won’t be able to hack it, right?Wrong. It is true that hackers won’t be able to see your SSID, but they can still see your WiFi signal just as you can still connect to it. As shown in the picture below (captured with WiFi analyzer on an Android phone), hidden SSIDs are still displayed in a WiFi scan, although the SSID is unknown.
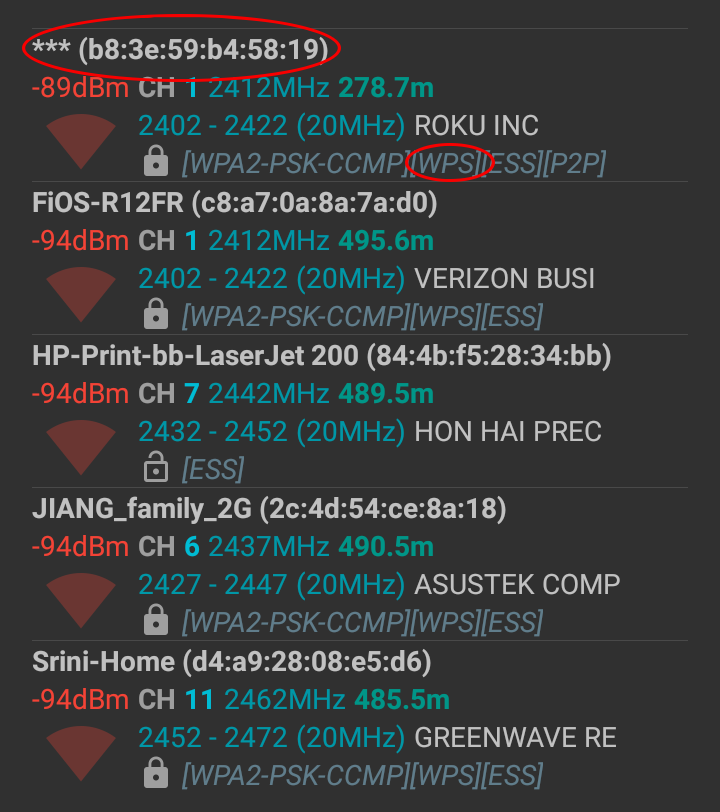
Finding out a hidden SSID only takes an appropriate set of tools and a few minutes time. The process has been documented many times on the web, for example here. And it has been demonstrated by a 3-minute video on YouTube.
- Enable MAC address filtering.
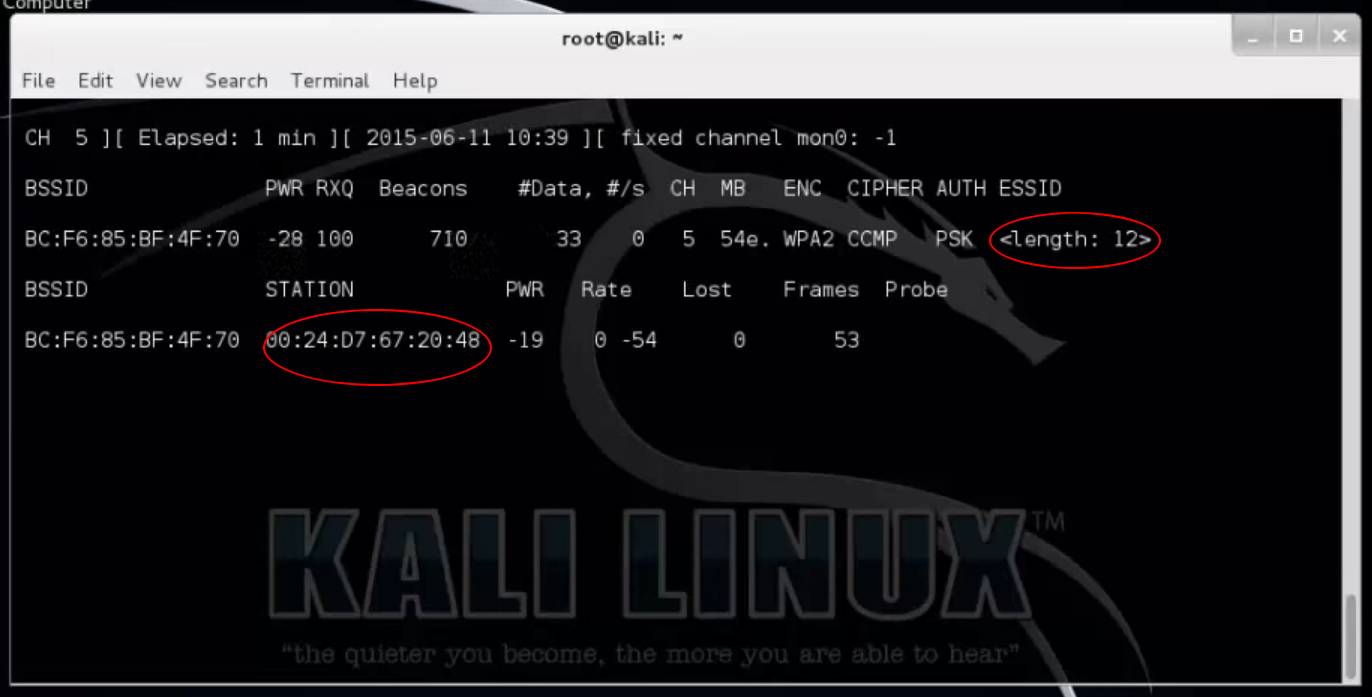
MAC address filtering is viewed as another security measure because it allows you to block or allow WiFi connection based on the MAC address of the device trying to connect. But again, this technique brings only superfluous value as far as securing your WiFi network is concerned. The reason being that it is easy to find out what MAC addresses are allowed by scanning your WiFi, and that it is just as easy to spoof a hacker’s device to take one of the allowed MAC addresses. The picture below shows the MAC address of a device connected to a router with hidden SSID (for which the length is shown), even before the SSID was uncovered.Our recommendation is, don’t even bother with MAC address filtering. It takes a lot of efforts to setup without much gain security wise.
- WPS (WiFi Protected Setup).
WPS is supposed to make it easier for you to connect devices to the WiFi router. But it also brought on vulnerabilities to an otherwise secure protocol (such as WPA2). Wikipedia documented many vulnerabilities found with WPS. In How to stop Wi-Fi hackers cold, the author described how a neighbor’s Wi-Fi router was used to engage in nefarious activities by exploiting WPS. The recommendation offered on routersecurity.org was:It is better to use a router that does not support WPS at all. If your does, try to turn it off, then verify that it really is off.
How do you verify that WPS is turned off on your router? You can find some tools from the routersecurity.org link above. If you have an Android phone, the “WiFi Analyzer” app can be used for that purpose (see the first picture in this post).
- WEP (Wired Equivalent Privacy).
One word: do not use it! WEP was found to be easily hackable. In my opinion, every router should drop support for WEP. But since there are still routers supporting WEP, I’m adding this warning. - WPA/WPA2 (WiFi Protected Access).
WPA/WPA2 currently is the only way to secure your WiFi connection. There are various combinations of WPA/WPA2 + TKIP/CCMP you can choose. Just remember that WPA2 is better than WPA, and CCMP (AES) is more secure than TKIP. You should always choose WPA2 with CCMP, unless you are forced to downgrade for compatibility issues arising from old devices.
In conclusion, there’s only one thing that really matters when securing your WiFi connection: WPA2 with CCMP.
- Disable SSID broadcast.