-
Beyond Three Dumb Routers
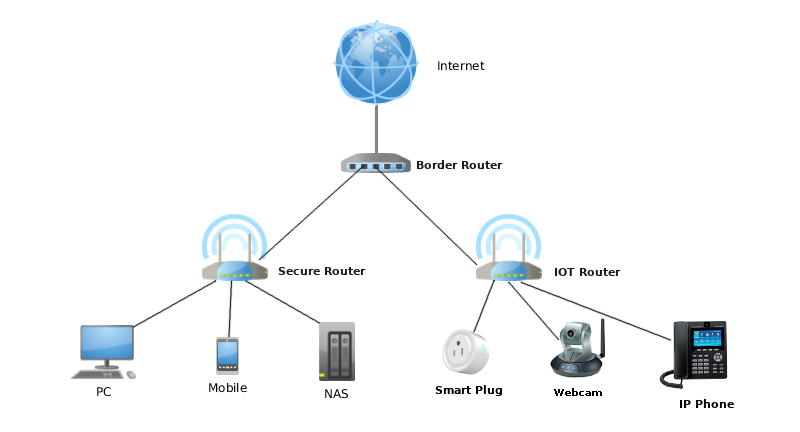
To mitigate the risks of IoT devices on your home network, Steve Gibson, the creator of ShieldsUP!, proposed a “Three Dumb Router” configuration to isolate the insecure IoT devices from your normal LAN, where the more valuable and more secure devices such as PCs and NAS storage reside. Since the devices stay in their own isolated networks, you stop the hacker from getting to you home PC or NAS even if your IoT device(s) get hacked.The setup was discussed in length in episode 545 of Security Now, and well documented on PC Perspective.
That’s the best way to go if you happen to have some dumb routers laying around and don’t want to invest in more expensive smart routers.
However, if you use the pcWRT router, we are going to show you below how to achieve network isolation and put more granular controls on IoT devices without additional hardware.
- Isolate IoT Network
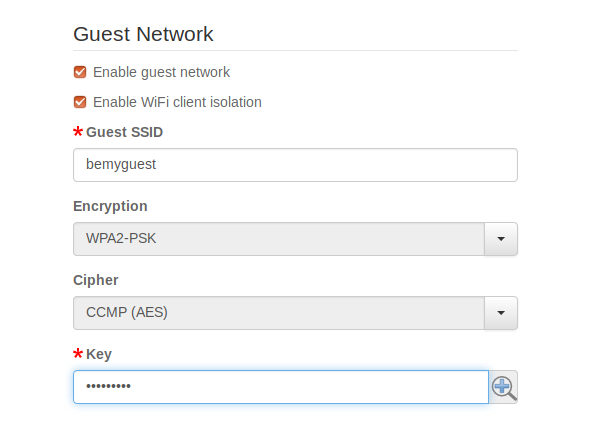
If your IoT device connects via WiFi, put it on the guest WiFi. In the pcWRT management console, you can create a guest WiFi network by checking “Enable guest network” on the Wireless Settings page. The guest network is isolated from the main WiFi network. Therefore, a compromised IoT device will not be able to find, connect to, or attack devices on the main network.You can optionally check the “Enable WiFi client isolation” checkbox, which blocks communication between devices connected to the guest network. This brings the additional benefit that a compromised IoT device cannot infect another IoT device connected to the guest network.
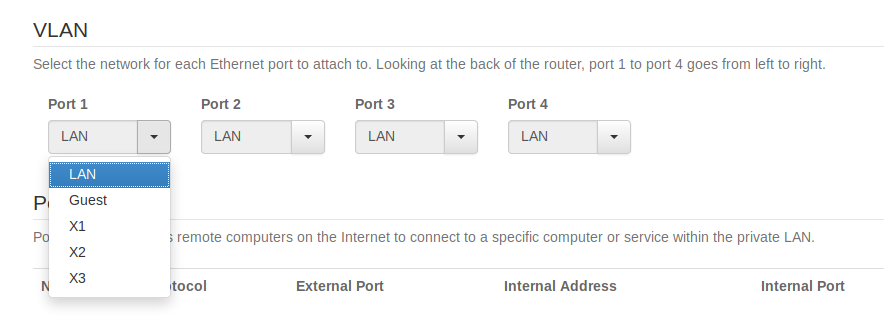
If your IoT device connects by wire, then you can put one of the Ethernet ports on the back of the router on VLAN and connect the IoT device to that port.You can choose the Guest VLAN or X1, X2, X3. However, if you want to isolate the IoT devices from each other (i.e., checked “Enable WiFi client isolation” in Wireless Settings), you need to choose X1, X2, or X3.
- Control Internet Access
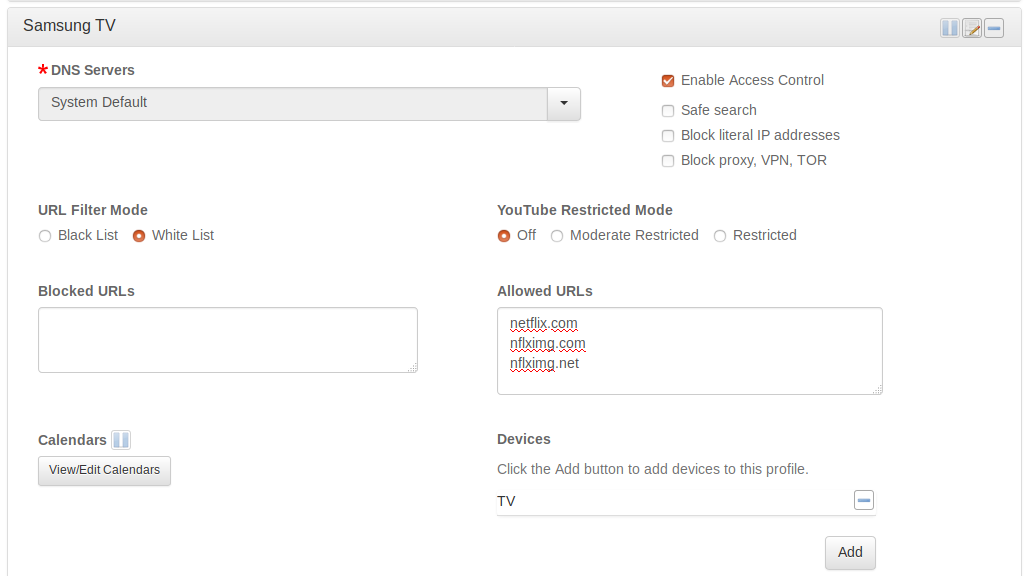
More likely than not, your IoT device only needs access to one or several domains to function. Thus you can restrict Internet access for your IoT device to a white list of allowed domains without affecting its functionality.Or you may intentionally omit some vendor domains if you suspect that the vendor is spying on you. For example, if you want to watch Netflix on your Samsung smart TV but don’t want Samsung and their third parties to hear your conversations, you can white list the Netflix domains only.
An additional advantage of using a white list is, even if your IoT device gets hacked, it cannot communicate back to the hacker’s C&C server.
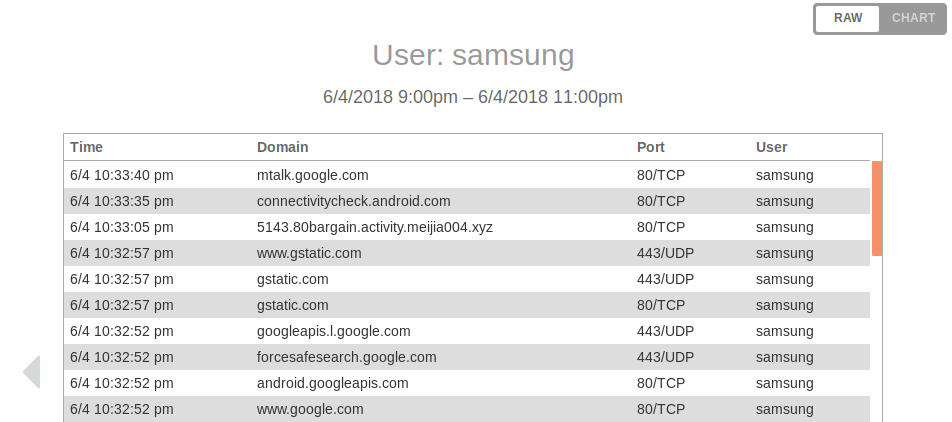
- Monitor Network Activity
With Access Control enabled, the pcWRT router logs every Internet request from the client device under control. You can monitor network activities of your IoT devices by viewing the Internet Logs. The router provides a summarized view displayed as a Chart and a detailed view with protocol & port in Raw mode.
- Monitor Bandwidth Consumption
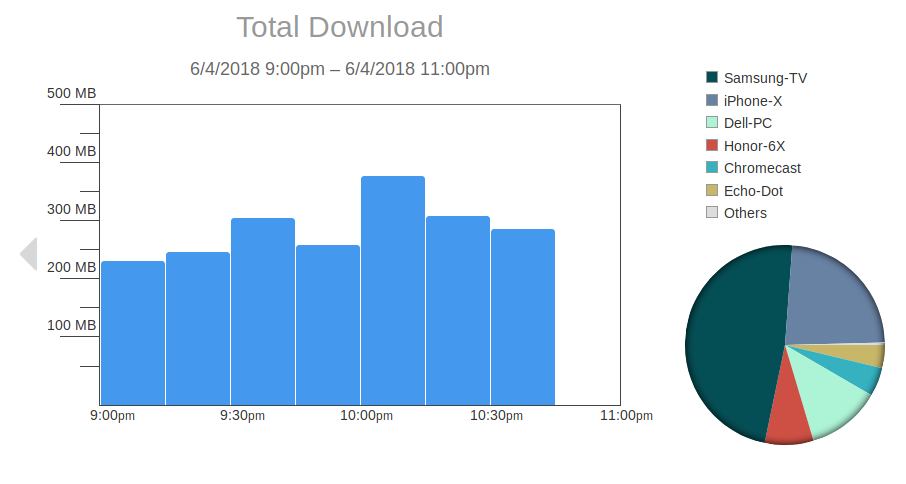
Do you ever wonder how much data is sent by your IoT devices? If you enable the bandwidth monitor, you’ll be able to see the download and upload bandwidth consumption for every device on your network, including your IoT devices.
- Isolate IoT Network













