-
Why DNS leak tests might fool you

What is a DNS leak test
Even after you connect to a VPN, your DNS queries might still be sent to your ISP instead of your VPN service. This situation is called a DNS leak. DNS leak tests will tell you who your DNS provider is. You’ll find multitude of DNS leak test sites when you search for “dns leak test“.
Usually, people assume that there’s no leak if the DNS servers reported by the DNS leak test are not that of their ISP.
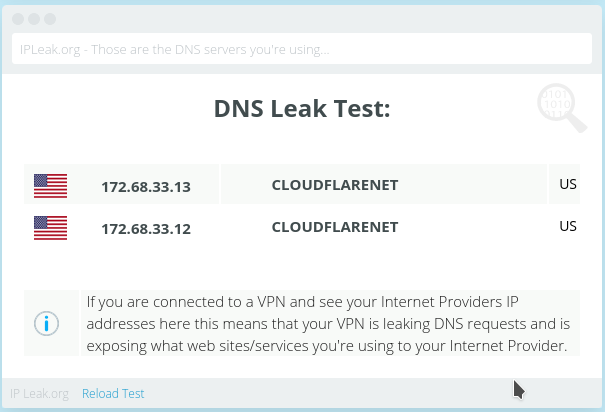
Why the DNS leak test might fool you
DNS leak tests tell you who your DNS provider is, but they don’t tell you how you reached your DNS service.
As a simple example, disconnect your VPN but set your DNS service to Cloudflare (IP addresses 1.1.1.1 & 1.0.0.1). Now run a DNS leak test. It’ll tell you that your DNS provider is Cloudflare.
Are your DNS queries protected? No. Your DNS queries are going through your ISP connection unencrypted. Your ISP is still able to monitor your DNS requests.
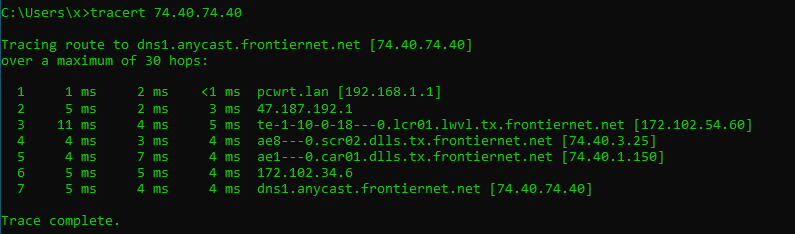
Using the
tracertcommand, you can see how you are reaching your DNS server.- The following tests are performed with VPN off.
- ISP DNS server
- Cloudflare through ISP
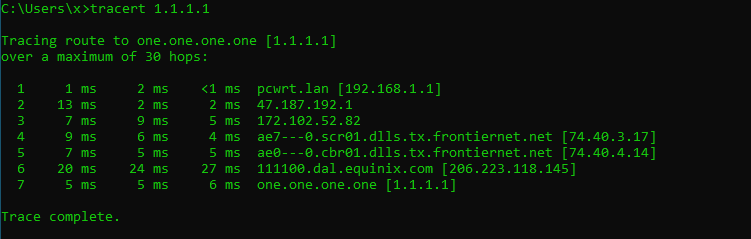
As you can see, in both cases the DNS requests will go through the ISP network.
- ISP DNS server
-
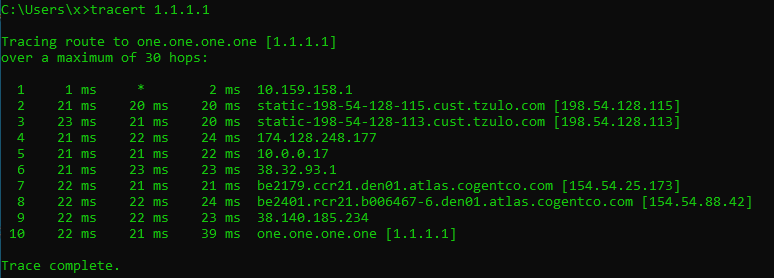
With VPN turned on (on the router):
- Cloudflare through VPN
- ISP DNS server through VPN
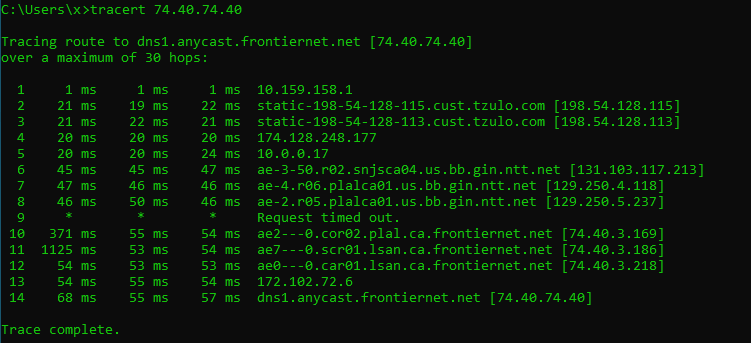
In both cases, your DNS queries will go through the VPN network. Even if you still use your ISP’s DNS servers, they won’t be able to associate those queries with you, because the DNS queries are coming from the IP address of the VPN server.
- Cloudflare through VPN
Conclusion
In order to make sure that your DNS queries are properly protected, you need to:
- Run a DNS leak test to make sure that your DNS service is what you set it to. I.e., your DNS service is not being hijacked (sometimes misleadingly called transparent proxying when an ISP does it).
- Run
tracertto make sure that you’re reaching the DNS servers through your VPN connection.
What to do if you can’t run
tracert? I offer two options here, but there may be other ways.- Connect your VPN to a remote server (e.g., Europe if you are in the US). Then run a DNS leak test and verify that the location of the DNS server is where your VPN server is.
- Run the DNS leak test twice, before and after you connect to the VPN. The results should be different.
- The following tests are performed with VPN off.







