-
Are you building a surveillance network around your house?

And letting others spy on you?Smart TVs, security cameras, smart thermostats, smart plugs, smart doorbells, Alexa Echo, Google Home. All of these are capable of collecting data from your home (network traffic, connected devices, shared files, image, voice, video, etc.), and capable of sending data out to anywhere over the Internet, uninhibited.
Earlier this year, a conversation between a husband and wife in the privacy of their home was recorded by Amazon Alexa and sent to a random person in the family’s contact list. This was how Amazon explained the incident:
Echo woke up due to a word in background conversation sounding like ‘Alexa.’ Then, the subsequent conversation was heard as a “send message” request. At which point, Alexa said out loud ‘To whom?’ At which point, the background conversation was interpreted as a name in the customer’s contact list. Alexa then asked out loud, ‘[contact name], right?’ Alexa then interpreted background conversation as ‘right.’ As unlikely as this string of events is, we are evaluating options to make this case even less likely.”
Amazon said that Alexa asked (loudly) for permission to send the recorded conversation, but according to the wife, the device did not audibly advise her it was preparing to send the recording.
The scary part of the story is, Alexa starts recording when it thinks it heard the wake up word. It sends a recording out when it thinks it heard your command to send. And, had the person receiving the recording not called back, the couple would have never known that their private conversation was recorded and sent out by Alexa.
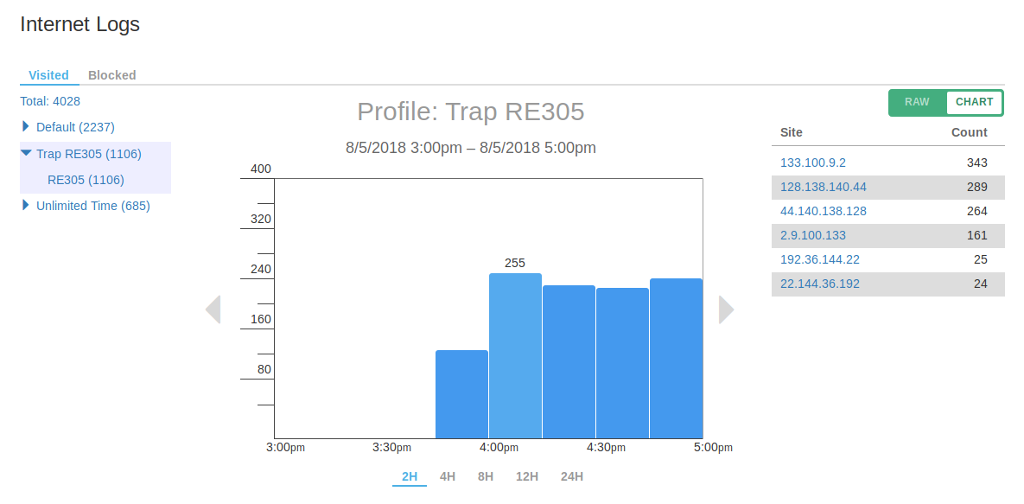
I recently bought a TP-Link RE305 WiFi range extender. But what happened after I plugged it in to my network gave me a big surprise.
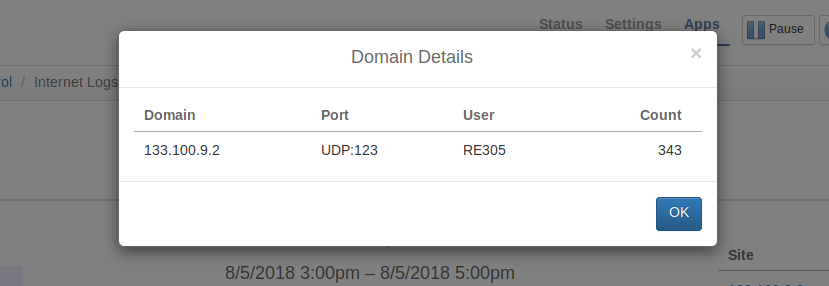
As you can see from above, the WiFi extender was sending about 250 requests to 6 random IP addresses every 15 minutes! It almost looked like a compromised device participating in a DDoS attack!
Looking at the details revealed that all these requests were sent out to NTP servers. And indeed those IP addresses belong to NTP services ran by various organizations. But still the huge number of NTP requests is an anomaly. There’s absolutely no reason to sync time every 3-4 seconds!
As it turned out, it was a bug in the TP-Link firmware. Upgrading to the latest version resolved the problem. The point is, you can never make assumptions about what a device will do on your network.
On your router, a firewall separates your internal network (LAN) from the outside (WAN). The firewall blocks outside requests to access your network unless you explicitly allowed it to (e.g., port forwarding, UPnP). By installing a device in your network, or an app on your smart phone, you immediately give the device/app all privileges on your internal network. This can bring several security risks to your network:
- These “smart” devices have minds of their own, they may capture info and send out whenever they want. For example, a video camera may take a video at an inconvenient moment.
- The device/app may be capturing sensitive information and send it back to the vendor. Reputable vendors don’t do this, but some do. One of the better known was the now defunct Carrier IQ.
- The device may be vulnerable to hacking, such as the multitude of devices compromised by the Mirai botnet.
- The device/app might be using an insecure protocol to communicate back to its server, making it vulnerable to snooping or being redirected to a malicious destination.
- Compromised devices, or malicious apps installed on your smart phone or computer have internal network (LAN) privileges to hack other devices on the network.
- You might have inadvertently agreed to a vendor’s T&C, thereby granting them lawful rights to snoop on you.
So what can you do to minimize your risks?
- Put less secure devices (i.e., so called IoT devices) on their own isolated networks. If you are connecting by WiFi, make sure that you turned on WiFi client isolation for these devices. If you are connecting by Ethernet wire, create a dedicated VLAN.
- Limit Internet access of these devices to the domains or hosts that are absolutely necessary for their functionality. Block everything else.
- Stop Internet connectivity for a device when you know you don’t need it. For example, when you are at home and don’t want your security camera to monitor yourself.
- Periodically monitor the Internet connectivity patterns and bandwidth consumption to spot any anomalies.
Update: After I finished this posting, I stumbled across a very interesting article on the same subject. Here you go: The House That Spied on Me.