-
A VPN Leak in Windows 10
This is not your normal DNS or WebRTC leak. It is observed that preexisting network connections keep communicating outside the VPN tunnel long after the VPN connection is established. It looked like the iOS leak reported earlier, but this one is more of a VPN client problem than an OS level problem. The challenge with this type of leak is, it is not detectable with your normal VPN leak tests. Since the leaked connections existed before the VPN connection is established, VPN leak tests will usually return a clean bill of health.
The tests were done on a Windows 10 computer running version 22H2. We connected to ProtonVPN using OpenVPN and WireGuard. Network activities were captured with the Internet Logs monitoring tool on the pcWRT router.
We tested the OpenVPN client v2.6.4 and ProtonVPN client version 3.0.5 for OpenVPN protocol and WireGuard protocol.
OpenVPN Client
With the OpenVPN client, the router logged a bunch of connections outside of the VPN tunnel after the VPN connection was established.
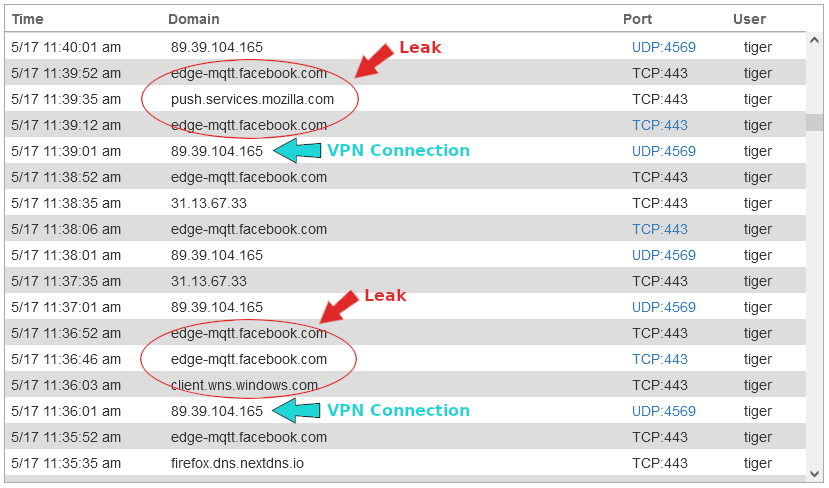
There were still multiple TCP connections outside of the VPN tunnel 40 minutes after the VPN was connected.
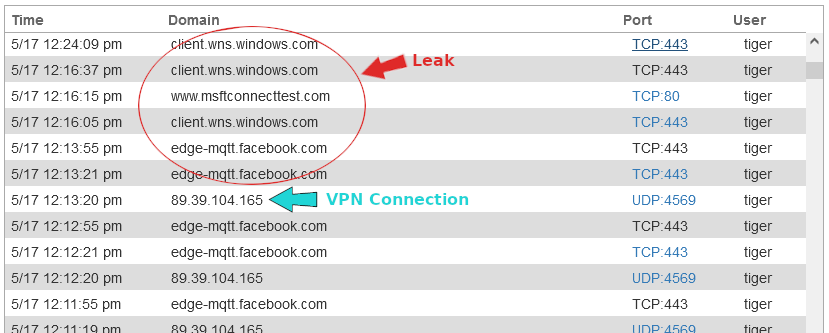
I left the VPN connected but let the computer go to sleep. When the computer woke up from sleep, the OpenVPN client reestablished the connection. But then more TCP connections leaked outside the VPN tunnel.
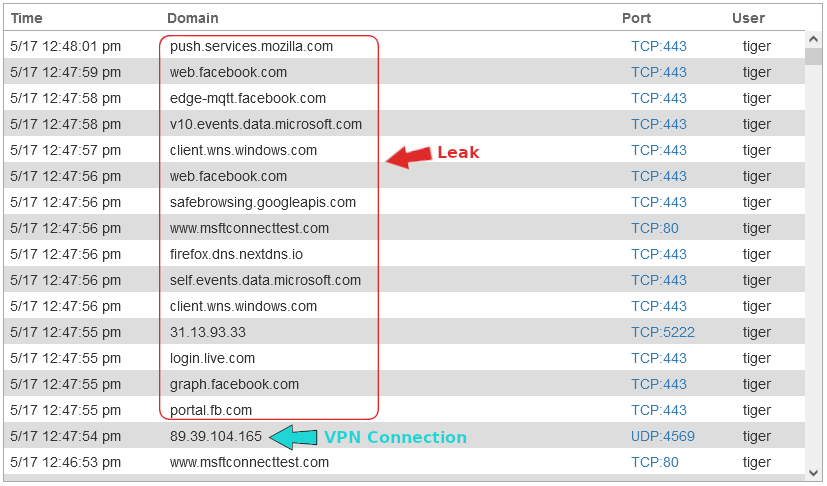
Maybe it is worth noting that the OpenVPN client does not have a kill switch, but leaking connections outside the VPN tunnel (while the VPN is connected) is probably unrelated to the kill switch.
ProtonVPN Client with OpenVPN and WireGuard
We tested the ProtonVPN client with both OpenVPN and WireGuard protocols. The results were the same so I’ll present one set of screenshots below.
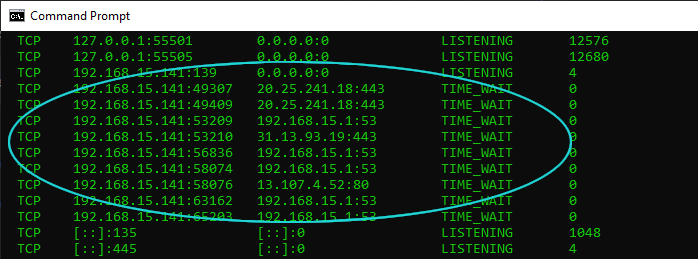
Unlike the OpenVPN client, the ProtonVPN client disconnected all existing connections once the VPN tunnel was established. The Internet logs on the pcWRT router did not report any long lasting connections outside the VPN tunnel. Running the “netstat” command on the computer also showed that the connections outside the VPN were closed. And this was without turning on the kill switch.
However, leaks were reported by the pcWRT router when the computer went to sleep and woke up, when the VPN was trying to reconnect. This happened with and without turning on the kill switch.
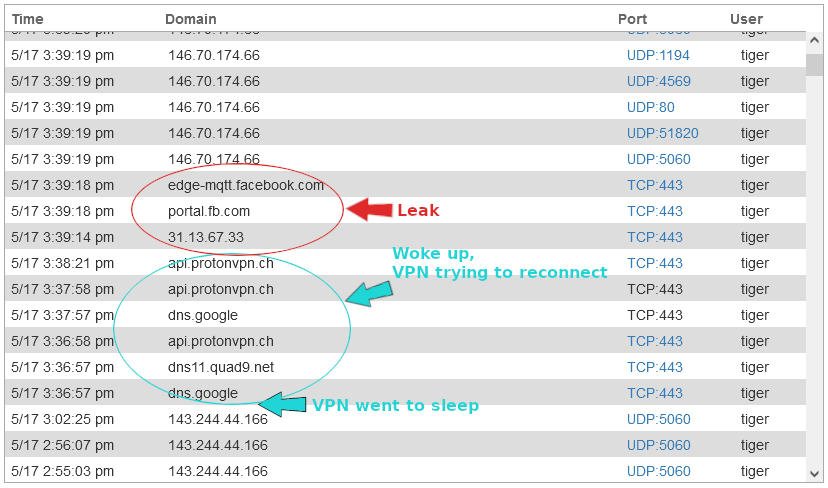
Connection leak when computer woke up from sleep and VPN was reconnected (without kill switch) 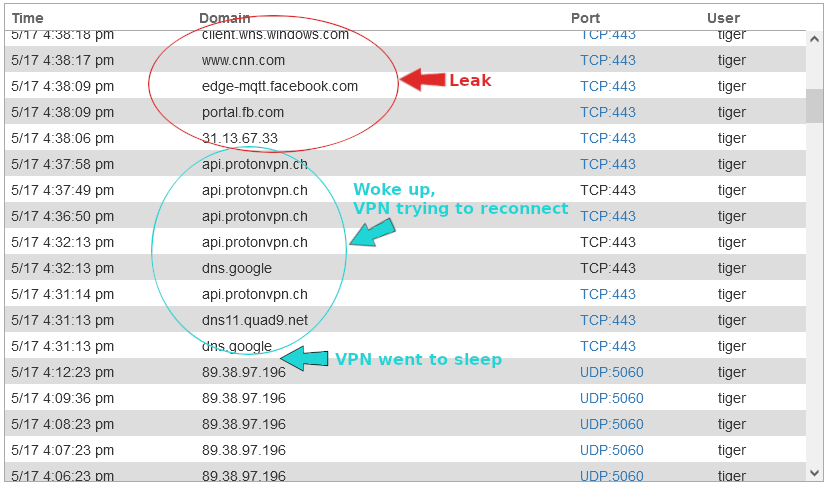
Connection leak when computer woke up from sleep and VPN was reconnected (with kill switch) ProtonVPN Client with Permanent Kill Switch
However, the ProtonVPN client comes with a second kill switch: the permanent kill switch. The permanent kill switch blocks Internet connectivity entirely when the VPN is not connected. It persists even after you shutdown and reboot the computer. If you want to connect to the Internet without VPN again, you must disable the permanent kill switch first.
With the permanent kill switch turned on, no VPN leak was reported by the pcWRT router when the computer went to sleep and woke up again.
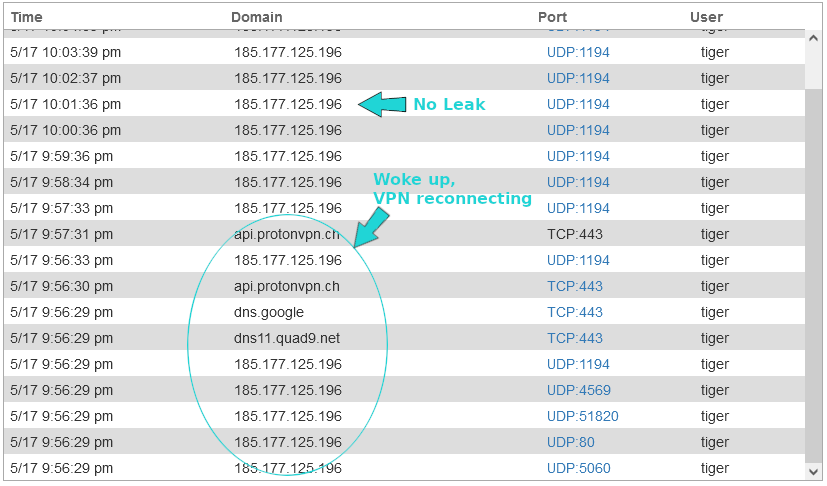
Is This Detectable with a VPN Leak Test?
In general, no. But if you configure your browser to use DNS over HTTPS, you might be able to see a DNS leak. As shown below, the computer was connected to a VPN server in the Netherlands but the detected DNS servers were from the US.
That’s because the HTTPS connection for DNS was established before the VPN connection, and the VPN connection was not able to shut it down and bring it inside the VPN tunnel.
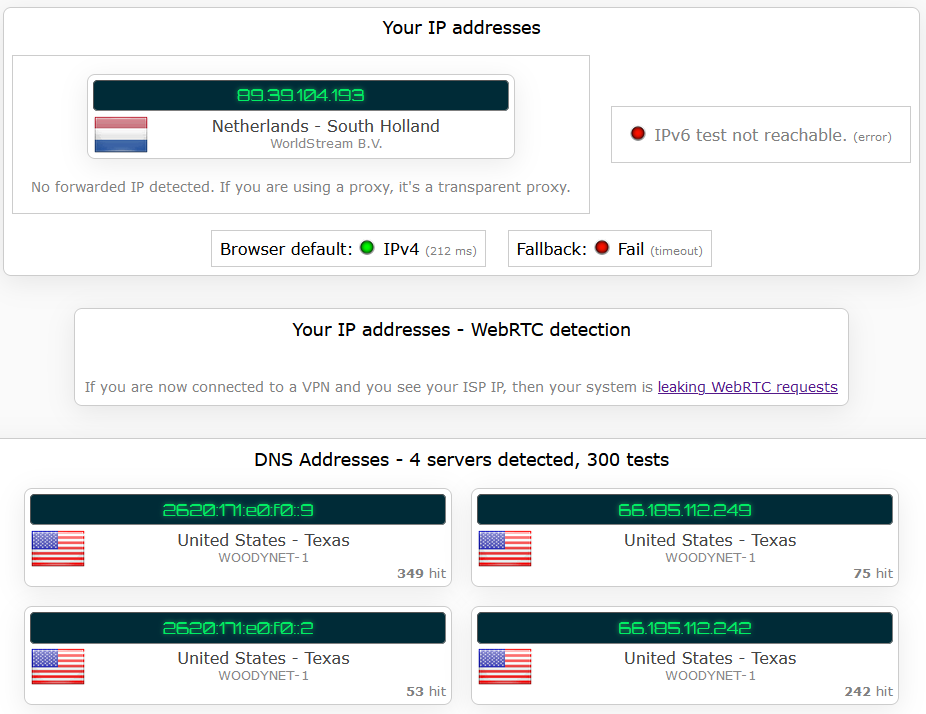
What Does This Mean for Privacy?
A false sense of security. You might be thinking that your communications are protected by a VPN tunnel but in fact some data are transmitted outside of it. Those outside communications might be the ones you want to protect.
As shown here, the leaking behavior depends on the VPN client application you’re using and how you configured the VPN client. The ProtonVPN client with permanent kill switch avoids leaks of this type. But what if you’re using a different VPN client app? You can’t be sure there’s no leak until it’s fully tested.
In general, it is safer to run the VPN client on a router to avoid VPN leaks of this kind.







