-
Oblivious DNS over HTTPS vs DoH through HTTP proxy
Cloudflare recently published a blog post on how Oblivious DNS over HTTPS (ODoH) works. According to the blog post, the purpose of ODoH is to separate the DNS queries from the originating IP addresses, preventing the DoH provider from seeing who’s sending the DNS requests. Thus improved privacy for clients.
Schematically, this is how it works:
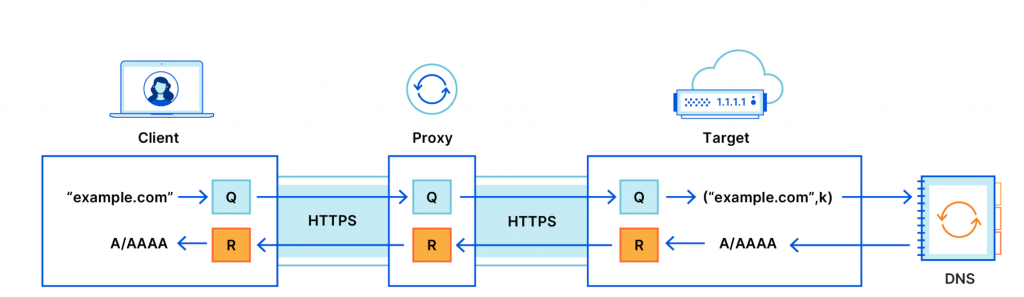
In the diagram above, you can safely assume that the “target” is the DNS resolver (such as 1.1.1.1). By introducing the proxy between the client and the target resolver, ODoH provides the following guarantees:
- The target sees only the query and the proxy’s IP address.
- The proxy has no visibility into the DNS messages, with no ability to identify, read, or modify either the query being sent by the client or the answer being returned by the target.
- Only the intended target can read the content of the query and produce a response.
However, it looks to me an overly round about way to achieve the three goals above. A plain old HTTP proxy seemed adequate enough to deliver the above three benefits.

The steps with a plain HTTP proxy are:
- Client sends HTTP CONNECT request to the proxy
- Proxy establishes TCP connection withe the target
- Proxy responds with “CONNECTION OK” back to the client
- The client starts a new HTTPS session with the target, with the proxy blindly ferrying the bytes back and forth between the client and the target (DNS resolver)
Now check the three guarantees provided by ODoH above against the plain HTTP proxy setup. Do you see a violation of any of them?







