-
6 VPN leak scenarios and how to prevent them
TL;DR: the pcWRT router naturally protects you from the 6 leak scenarios listed below (i.e., no extra work needed). But if you’re using another VPN solution, read on.
1. DNS Leak
DNS Leak is the most common type of leak when you are connected to a VPN. Even after your VPN is successfully connected, there’s a possibility that your DNS queries are sent outside the secure tunnel established by the VPN. As such, your ISP or the owner of the WiFi hotspot you are connecting to (or anyone sitting between you and the Internet) can still see which websites you are visiting.
The usual way to test this is to see who is your DNS service provider, and there are plenty of websites that would allow you to run this test. After connecting to a VPN, if you still see your ISP as the DNS provider, then you definitely have a leak. On the other hand, if you see that a third party is providing your DNS service, it is normally assumed that you don’t have a leak.
However, as shown in another post, there are situations in which these tests give you a false sense of security. Since the general idea is covered by the other post, I’ll just give you one specific example here without repeating what’s been said there.
A lot of people use Pi-hole to block ads. When they start a VPN connection on the PC, the ad-blocking functionality provided by the Pi-hole is lost. One way to bring back the Pi-hole ad-blocking is to set a custom DNS on the VPN. I.e., set the DNS IP address for the VPN connection to that of the Pi-hole.
However, doing so brings a DNS leak as shown in the picture below. While your normal Internet traffic is tunneled through the VPN as usual (the blue line), the DNS traffic is routed to the Pi-hole then forwarded to the upstream DNS service (the red line). Since the Pi-hole is outside of the VPN tunnel, your DNS traffic is routed through the ISP gateway in clear text – i.e., a DNS leak.
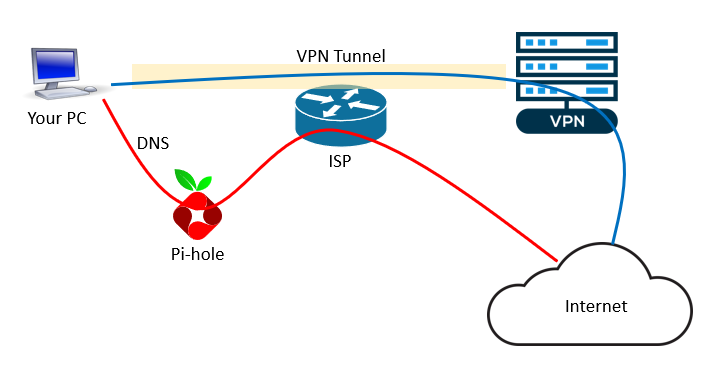
How to prevent DNS leak
- Use a VPN client that does not leak DNS
- If you have to use a DNS outside of the VPN tunnel, such as the Pi-hole example above, consider setting up a DNS proxy (such as Cloudflared) to encrypt your DNS queries to the upstream servers.
2. IPv6 Leak
Maybe you don’t know, but your computer might have two IP addresses when it is connected to the Internet: one IPv4 address and one IPv6 address.
IP leak test sites usually will show both your IPv4 and IPv6 addresses. If the IP leak test site only tests for IPv4, switch to a different test site.
Sometimes the test tells you that you don’t have an IPv6 address, then you don’t need to worry about IPv6 leaking. If both IPv4 and IPv6 addresses are displayed, make sure that both IP addresses are from your VPN service.
How to prevent IPv6 leak
In case there is an IPv6 leak, you can disable IPv6 on your computer.
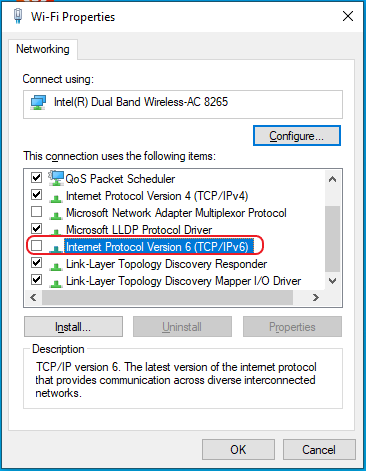
On Windows,
- Go to the Network Connections dialog
- Bring up the Properties dialog for the WiFi or Ethernet adapter
- Uncheck “Internet Protocol Version 6 (TCP/IPv6)”
3. WebRTC Leak
WebRTC is a protocol that “allows audio and video communication to work inside web pages by allowing direct peer-to-peer communication, eliminating the need to install plugins or download native apps”. It is supported by all major browsers.
In some cases, WebRTC may accidentally leak your real IP address. Again, you can use the IP leak test sites to test for WebRTC leak. Make sure the page doesn’t display your IP address assigned by the ISP.
How to prevent WebRTC leak
If you detect WebRTC leak, you need to disable WebRTC in your browser. Here’s a link that gives instructions on how to disable WebRTC in major browsers: How to disable WebRTC in Chrome, Firefox, Safari, Opera and Edge.
4. Dropped VPN Connection
If you are on a VPN and the VPN connection is interrupted or dropped for whatever reason, your Internet traffic falls back to the default ISP connection. Therefore, leaking your real IP address.
To guard against leaking when VPN connection is down, you’ll need to use a VPN client that has a “kill switch”. When the “kill switch” is enabled., the VPN client will shutdown your Internet connection (instead of falling back to the ISP connection) whenever the VPN connection is gone.
5. Programs Started Before VPN
Even with a “kill switch”, there is a chance of IP leaking when you auto-start programs and the VPN. Your applications might reach out to the Internet before the VPN is started, thus leaking your real IP address.
To prevent this leaking scenario, you probably want to delay the starting of the applications that need VPN protection (e.g., switch them to manual start).
Some applications offer the option to bind to a specific network interface. Make sure you bind them to the VPN interface to prevent IP leak.
6. Application Specific Leaks
Just like a browser can leak your real IP address via WebRTC, an application can leak your IP address because of the way it works. For example, a user reported that qBittorrent was using both his real IP address and his VPN IP address with the default configuration.
In general, application specific leaks are not detected by websites that detect IP leaks. You’ll need something like Wireshark to detect such leaks.
But for BitTorrent clients there’s an easier way: ipMagnet.
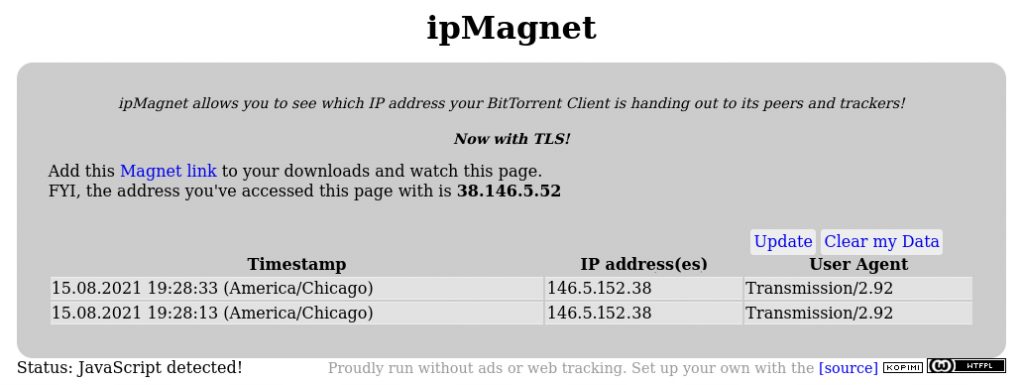
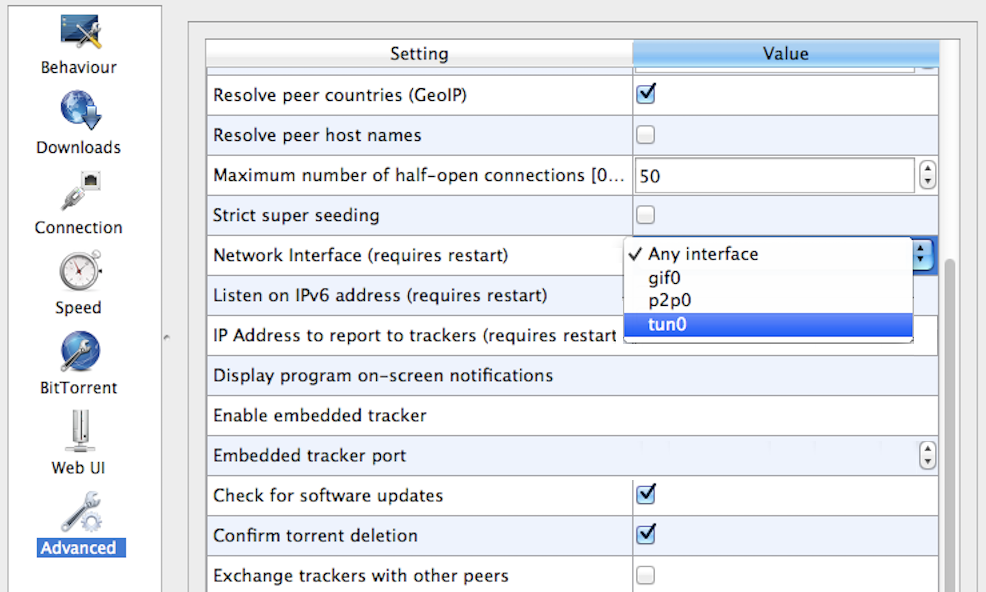
By default, qBittorent binds to all network interfaces found on your computer, and that’s why it leaks your real IP address. To stop the above leak, you need to bind qBittorent to the VPN interface only. By doing so you’re also blocking the possibility of leaking in case your VPN starts after qBittorrent is started. Here are the steps:
- Turn on your VPN client
- Look for the VPN network interface in your Network Settings dialog
- Go to the advanced options of qBittorrent (Menu > Tools > Options > Advanced)
- Change the ‘Network Interface’ option to the interface you found in step 2
- Click on ‘Apply’ and restart qBittorrent
Our Recommendations
Due to the many possibilities of IP leaking, we recommend running your VPN client on a router when possible. It brings several advantages over running the VPN directly on your computer:
- You only need to set up the VPN once on the router for all your devices to use. It counts as one device to your VPN service provider.
- You can safely use your Pi-hole for ad blocking without worrying about DNS leak or needing extra software to encrypt your DNS traffic.
- VPN on router naturally blocks WebRTC leaks. So no need to disable WebRTC in all of your browsers.
- Once VPN kill switch is set up on the router, you don’t need to worry the sequence of auto-start programs on your computer.
- IP leaks caused by applications are effectively blocked.







