Category Archives: Security
-
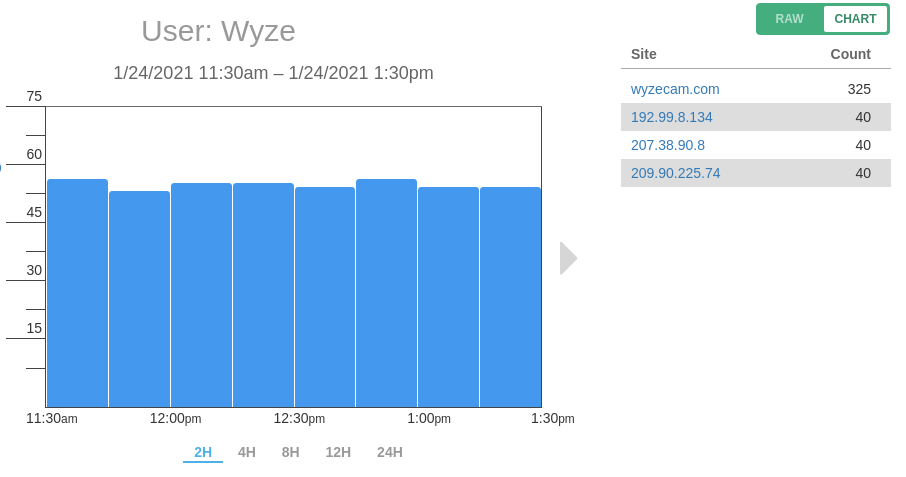
Is WyzeCam Sending Data to Servers Other Than AWS?
Posted on January 26, 2021 by pcwrt in Security, Technology.When the WyzeCam started selling a few years back, there was an alarming review on Amazon stating that it was sending data all over the world. The reviewer claimed seeing traffic heading to China, Japan and Germany, among other locations. The review on Amazon is probably no longer available. But the discussion on Reddit is […]
Continue Reading... No Comments. -
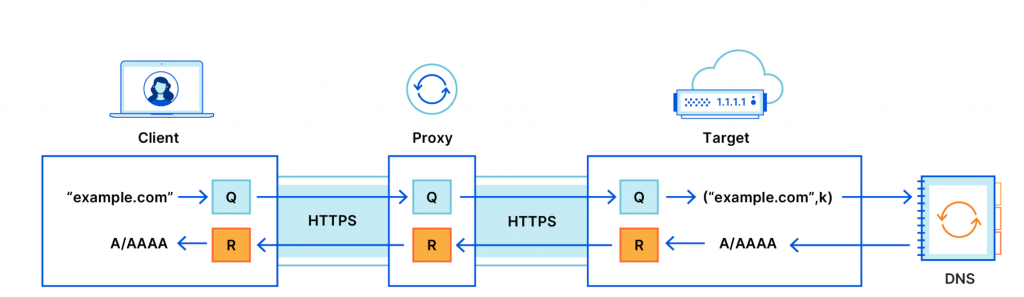
Oblivious DNS over HTTPS vs DoH through HTTP proxy
Posted on December 9, 2020 by pcwrt in Security, Technology.Cloudflare recently published a blog post on how Oblivious DNS over HTTPS (ODoH) works. According to the blog post, the purpose of ODoH is to separate the DNS queries from the originating IP addresses, preventing the DoH provider from seeing who’s sending the DNS requests. Thus improved privacy for clients. Schematically, this is how it […]
Continue Reading... No Comments. -

Why DNS leak tests might fool you
Posted on August 8, 2020 by pcwrt in Security, VPN.What is a DNS leak test Even after you connect to a VPN, your DNS queries might still be sent to your ISP instead of your VPN service. This situation is called a DNS leak. DNS leak tests will tell you who your DNS provider is. You’ll find multitude of DNS leak test sites when […]
Continue Reading... No Comments. -

Is it safe to enter credit card info on public WiFi?
Posted on May 11, 2020 by pcwrt in Security, Technology, WiFi.How big is the risk? Time and time again you’ve been told that public WiFi hotspots or compromised routers will get your credit card numbers and banking info stolen. However, such risks have been overly hyped. We agree that public, open WiFi networks totally cannot be trusted. And that compromised routers can be used to […]
Continue Reading... 1 Comment. -

Monitor activities on your home network
Posted on May 6, 2020 by pcwrt in Parental Control, Security.The pcWRT router provides two ways to monitor your network activities. You can view every site visited (or blocked) by each device (or user) by clicking the “View Logs” link on the Access Control page. And you can view the bandwidth consumption of each device on the Bandwidth Monitor page. Access Logs Click the View […]
Continue Reading... 3 Comments. -

Ad blocking on your home network (and in apps)
Posted on May 2, 2020 by pcwrt in How To, Router, Security.Problems with ad blocking browser extensions Browser extensions are the most popular tools for ad blocking. However, they have a few drawbacks. Browser extensions bring higher security risks. In fact, a few popular ad blocker extensions were found to be malicious and were removed from the Chrome Web Store recently. They only work inside the […]
Continue Reading... 6 Comments. -

Concerned about privacy? Don’t bother to reset your advertising ID
Posted on February 21, 2020 by pcwrt in Security.What is the advertising ID? The advertising ID is an identifier on your mobile device that is created to identify you for advertising purposes. It is present on both Android and iOS devices. Apps on your mobile devices can send your behavior along with the advertising ID to one or more advertising networks. By linking […]
Continue Reading... No Comments. -

How to set up an OpenVPN client connection on the pcWRT router
Posted on December 24, 2019 by pcwrt in How To, Router, Security.Setting up a VPN connection on the router is not an easy task. First of all, not many routers support VPN. If your existing router does not support VPN out of the box, you might need to flash it with open source firmware so that you can install VPN software on it. Then you need […]
Continue Reading... No Comments. -
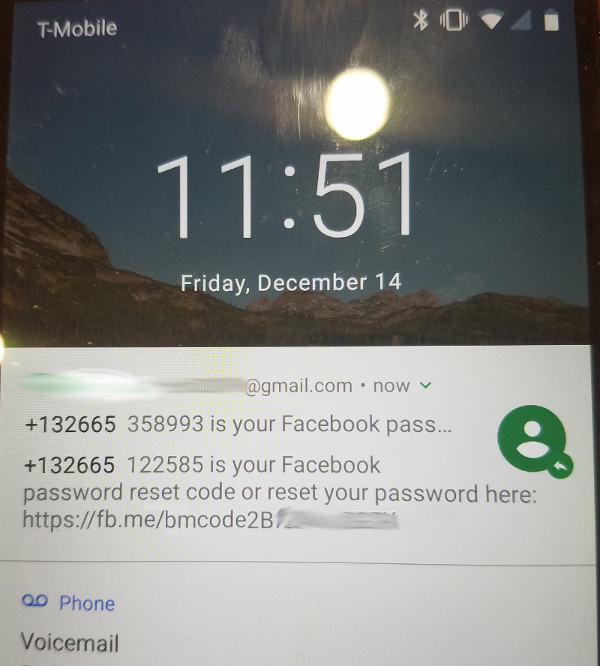
Why it’s a bad idea to show all notification content on Android lock screen
Posted on December 14, 2018 by pcwrt in How To, Security, Technology.By default, Android displays notification content on the lock screen. While it may seem like a convenient feature at first, it’s probably a bad idea. This is what my lock screen looked like after I requested a password reset on Facebook: Looks scary? Here’s how to turn it off: Open the Settings app Tap on […]
Continue Reading... No Comments. -
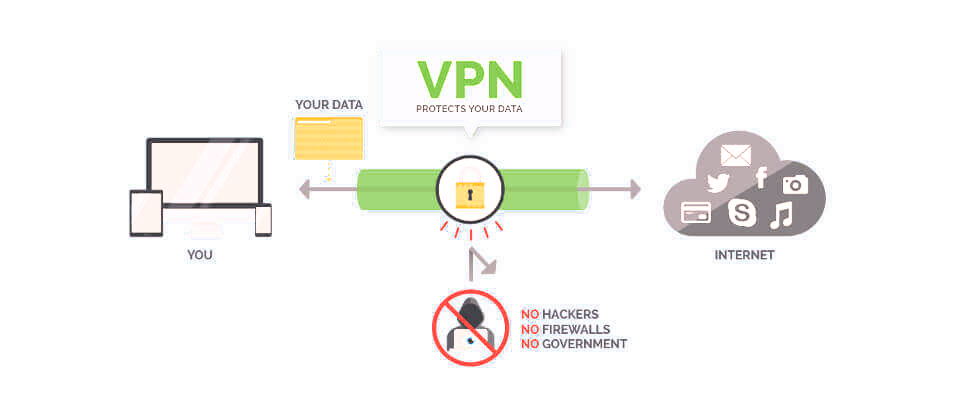
Does a VPN Really Protect My Privacy?
Posted on August 19, 2018 by pcwrt in Security, Technology.The above picture is often used to illustrate how VPNs can protect your privacy. Because the VPN creates an encrypted tunnel between you and the Internet, your privacy is protected. However, the picture is missing a very important piece: the VPN service provider. As you can see, the encrypted tunnel ends at the VPN service […]
Continue Reading... No Comments.




