-
Ad blocking on your home network (and in apps)
Problems with ad blocking browser extensions
Browser extensions are the most popular tools for ad blocking. However, they have a few drawbacks.
- Browser extensions bring higher security risks. In fact, a few popular ad blocker extensions were found to be malicious and were removed from the Chrome Web Store recently.
- They only work inside the browser. So you need to install them in each browser you use, and on every device you use.
- They don’t stop ads in apps.
Set it up for your network (the pi-hole way)
You’ve probably heard of Pi-hole, an open source software package that runs on a Raspberry Pi and blocks ads on any device connected to your network. Pi-hole works by blocking the DNS resolution of the advertising servers. As such, it cannot block ads served from the same domain as the content. But nonetheless it is very effective at blocking the worst kind of advertising: the tracking cookies that follow you everywhere you go.
While pi-hole is efficient and cost effective, it does require you to have some technology know-how. And things can get quite complicated when you throw VPN into the mix.
This is a detailed write-up if you are interested in setting up Pi-hole by yourself:
Install Pi-hole on Raspbian Lite From ScratchAd blocking with pcWRT
As of version v1.27, we’ve added Ad blocking to pcWRT. Behind scenes, we use the same technology Pi-hole uses. But the best thing is, you can easily enable it with a single click on the Access Control page. And if you need access to a domain that is blocked by the built-in list, just add it to the Allowed URLs box to bypass the blocking.
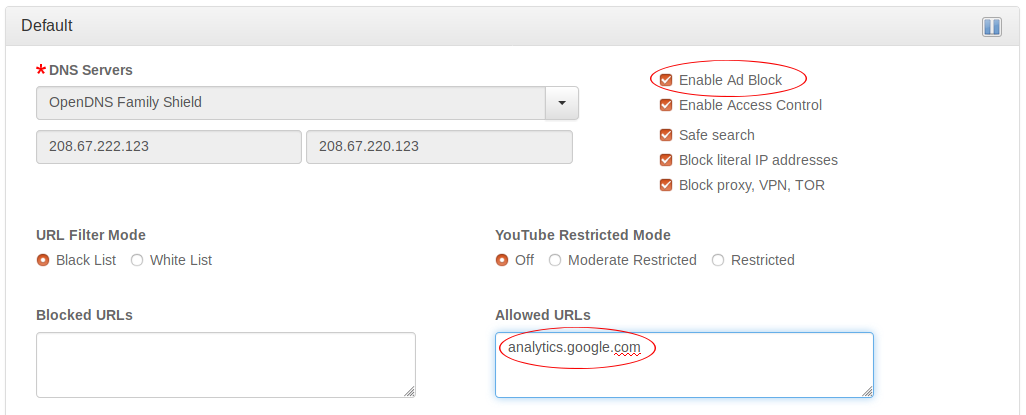
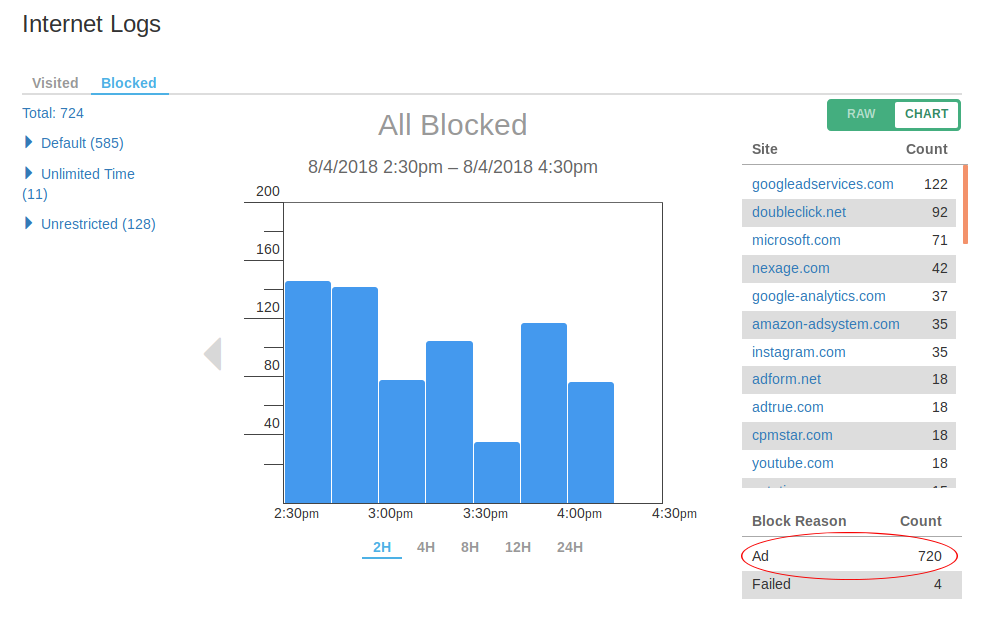
The domain names and number of requests blocked are reported in the Internet Logs page.
Pause or suspend when you need
One of the drawbacks for technologies like pi-hole is, there’s no easy way to unblock domains that need to be unblocked. First of all, you have to find out which domains need to be unblocked. Then you need to whitelist the domains (in the pi-hole console, for example). Thirdly, you may need to repeat the previous two steps until it works. These steps are usually out-of-reach for the ordinary user.
Occasions may also come up that you need to temporarily unblock some domains, or open up ads entirely.
As of version v2.0.6, we’ve added a link on the router login page for the user to suspend/pause/resume ad blocking on demand. The actions taken affect the current user only. For example, if Joe clicks suspend ad blocking on his computer, it is suspended only for him. Other users on the same network still has ad blocking enabled.
For easy access, it is recommended that you bookmark the Ad block Control page in your browser.
What to do when you go outside?
Apparently, when you are outside of the house, the ad blocking functionality you set up on your home network is no longer effective. However, since the pcWRT router has built-in support for VPN server, you can bring it on the road with you by setting up a VPN server and connect back to the house.
If you use Pi-hole, you can achieve the same with a pi-hole + pivpn combination.











Are you getting any performance complaints? I’ve had to disable it on mine because ping times go to heck in a handbasket.
Impact on performance should be negligible, especially ping. Blocking occurs at DNS lookup, so no impact on ping response time.
Specifically, what are your observations?
Hi. I also had to disable adblock on mine. For example I was going to visit a NYTIMES article posted on FB, but somehow ad.doubleclick.net was being used to route in between them. So it blocked the visit entirely.
I suppose I understand the technology that allows this to happen, but the functionality I was hoping for was that it would prevent ads from displaying within a page. (Somewhat like the Adblock Plus extension does in the Chrome browser. It doesn’t prevent you from visiting a site entirely, it just block the intrusive ads within the website.)
Ideas? Am I doing anything wrong?
Just like pi-hole, the router blocks ads by blocking requests to domains serving ads. This is different from browser side technology that actually downloads ad content but does not display it.
On the router, doubleclick.net has been identified as a domain that serves ads, and it is blocked as a result. This has the side effect of blocking access to contents delivered through doubleclick.net. But the upside is, it also blocks the tracking cookies that follow you around the web. Browser side ad blockers, while offering more flexibility on how the web page is rendered, does not stop the tracking cookies.
If you want to open up a domain that serves ads (with Ad block on), you may add the domain (e.g., doubleclick.net) to the white list.
What lists are you using for the default blacklist?
It’s mainly a combination of Steven Black’s list, Malware Domains and Cameleon hosts, augmented with our own list. The file has been uploaded to GitHub: https://github.com/pcwrt-router/Adblock.