-

Can Alexa be used to spy?
Posted on June 5, 2018 by pcwrt in Security, Technology.On May 24, 2018, Portland, Oregon local TV station Kiro 7 reported that an Amazon Alexa device recorded a private conversation, then sent it out to a random contact. Amazon confirmed the incident, and attributed it to an “unlikely” string of events that caused Alexa to mistakingly interpret background sounds as commands. In other words, […]
No Comments. Continue Reading... -
Put IoT devices on guest network
Posted on June 3, 2018 by pcwrt in Security, Technology.IoT devices are known to be vulnerable to cyber attacks. The best known instance of such an attack is probably the Mirai botnet. The botnet infected numerous IoT devices (such as home routers and IP security cameras) and used them to perform a Distributed Denial of Service (DDoS) attack. It brought down major web sites […]
No Comments. Continue Reading... -

Who is connected to my WiFi router?
Posted on January 20, 2018 by pcwrt in Router, WiFi.Are you worried that someone is connecting to your WiFi router without your permission? Well, if you are securing your WiFi with WPA2-AES (CCMP) encryption and a fairly strong password, you should be confident that no one is able to connect to your WiFi without knowing your password. Not even with the most recent KRACK […]
No Comments. Continue Reading... -

4 Tests You Should Do on Your WiFi Router to Avoid Hacking
Posted on January 19, 2018 by pcwrt in Router, Security, WiFi.In a previous post, I talked about how to secure your router WiFi. That’s only half of the puzzle. Another type of attack on your router comes directly from the Internet, without the need to connect to your WiFi signal. Due to the various security flaws on the home WiFi router, and the fact that […]
No Comments. Continue Reading... -

Five WiFi security settings and their effectiveness in securing your WiFi network
Posted on November 13, 2017 by pcwrt in Router, Security, WiFi.Technologies change fast, what was once considered safe and secure may become vulnerable and obsolete by today’s standards. Here I’ll show five wireless security settings generally available on a WiFi router, and their effectiveness in securing your WiFi network. Disable SSID broadcast. It is often recommended that you should disable SSID broadcasting to make your […]
No Comments. Continue Reading... -
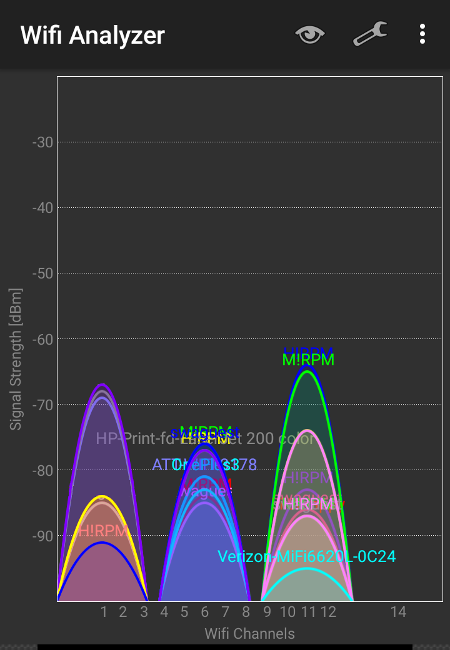
How to avoid bad WiFi connection by changing the channel on your router
Posted on October 16, 2017 by pcwrt in How To, Router, WiFi.When WiFi connections become slow, the first thing many people do is to buy a better, more powerful router. But many times the problem can be avoided by simply changing the WiFi router to another channel. There are two factors affecting WiFi performance, distance and radio frequency interference (RF interference). In contrast to people’s intuitive […]
No Comments. Continue Reading... -
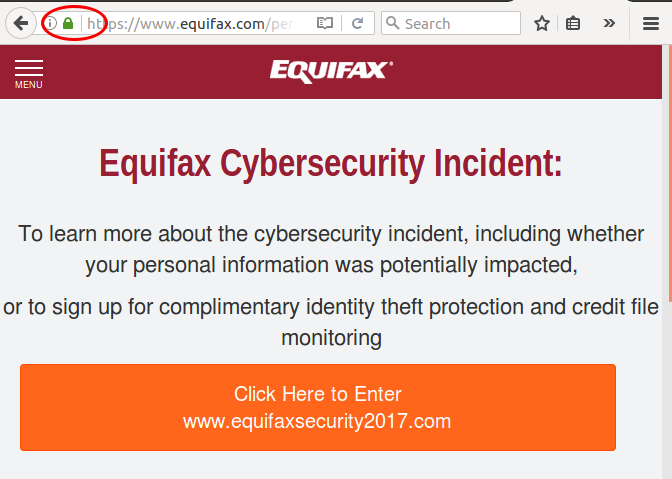
Is equifaxsecurity2017.com legit?
Posted on September 9, 2017 by pcwrt in News, Security.Big news that Equifax leaked personal info of 143 million Americans. In the wake of the news, people were directed to check their status at the website www.equifaxsecurity2017.com. The domain name sounded fishy, in the same sense as someone claiming that ebay-security-alerts.com is an official Ebay site. So a lot of people are asking whether […]
1 Comment. Continue Reading... -
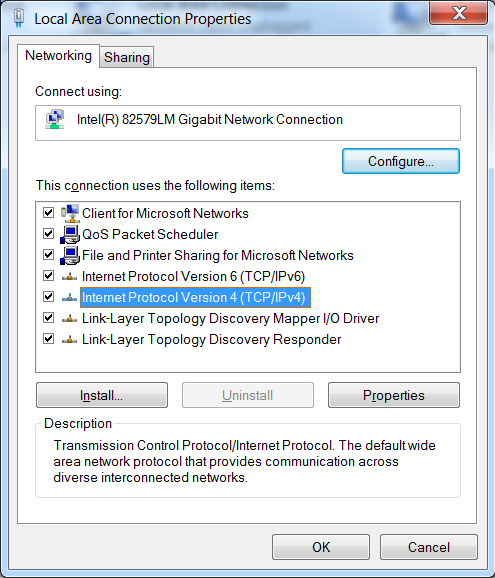
How to flash the Torch router with pcWRT
Posted on August 4, 2017 by pcwrt in Router, Technology.What you need: Download the firmware image from here. MD5 checksum: e2f1bb281dd9f78cd603faf515491548. A TFTP server. You can use PumpKIN if you don’t have a favorite one. Download the appropriate binary for your operating system. The steps (using Windows as example below). Configure your Ethernet address: open Windows network center, click “Change adapter settings”. Find […]
28 Comments. Continue Reading... -

The demise of Jawbone, a case of crappy products
Posted on July 14, 2017 by pcwrt in News, Technology.Jawbone, invested by top-tier venture capital firms such as Sequoia Capital and Andreessen Horowitz, once valued at more than $3bn, closed its doors, leaving customers hanging. Some attributed its failure to “overfunding“, others blamed a shrinking wearables market. But in our opinion, the reason is simple and dry – it’s a case of crappy products. […]
No Comments. Continue Reading... -

The Torch router is dead, and why pcWRT is better
Posted on June 2, 2017 by pcwrt in News, Technology.The Torch Router started out as a Kickstarter campaign in October 2015, and started shipping in October 2016. On May 9, 2017 some Torch users received emails informing them that Torch ceased operations. On May 31, 2017 it went completely dark, to the dismay of many. Since we also offer a parental control solution on […]
5 Comments. Continue Reading...













